Microsoft Sentinel
In 2019 Microsoft launched Microsoft Sentinel; security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution. That is quite a mouthful so let us break down what it can do for you and your company’s security!
Microsoft Sentinel is available in the Azure portal and aims to bring all your information to one place by connecting to existing applications and infrastructure, both from on-premises and multiple cloud vendors. Once connected, Microsoft Sentinel can make use of sophisticated security analytics and threat intelligence to inform you of both existing and new security threats.
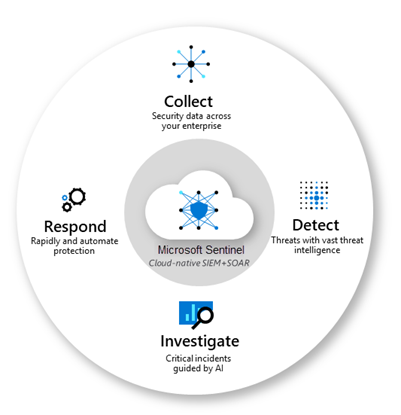
Microsoft Sentinel is built up of 4 main capabilities:
- Collecting data across your entire (hybrid) organization
- Detecting threats using threat intelligence
- Investigate threats with artificial intelligence
- Respond to incidents rapidly
Microsoft Sentinel offers connectors for Microsoft solutions and an increasing number of non-Microsoft solutions, as well as being able to use common event formats like Syslog and REST-API.
Some of the more popular connectors include:
- Microsoft 365 defender
- Office 365
- with Azure Active Directory
- Microsoft Defender for Identity
- Azure Web Application Firewall
Other vendors:
- Amazon Web Services
- Palo Alto Networks
- Cisco ASA
- Checkpoint
- Barracuda
- Fortinet
Unlike most other SIEM systems, Microsoft Sentinel does not only protect your office environment, but it can also be used to protect industrial environments. Using the Microsoft Defender for IoT connector you can add both industrial soft- and hardware to Sentinel!
Once your data sources are connected you can start to monitor the data using workbooks. Workbooks allow you to set alerts based on certain conditions; there are predefined workbooks that will include most used monitoring values, but you also have the versatility of being able to create your own custom workbooks.
Analytics are used to reduce the number of actionable alerts; Microsoft Sentinel will group alerts into an incident that can be investigated and resolved. You can make use of the built-in correlation rules or use them as a starting point to create your own rules.
Microsoft Sentinel also provides machine learning rules that can be used to map your network behavior and look for any anomalies that occur; matching multiple lower tier alerts from different entities to identify a potential high risk security incident.
You can respond to most of the threats directly in Sentinel or in the connected application by using a link from the alert. It is possible to automate some of your common tasks, a good example would be to create a ticket when a certain event occurs.
Additionally, there are more features that allow security administrators to perform further investigation and hunting capabilities!